Thursday, 19 December 2019
cattools not backing up
I found the issue was in the banner the config had used ^C for the banner marker and it seemed to be causing an issue.
Removed it and all was good.
Tuesday, 17 December 2019
checking for packet loss
ping 8.8.8.8
ISP's often have a direct connection to google from their network so its best to try ping an IP that will traverse the internet like ping a server in the UK or Australia
ping the gateway
pathping -n -4 x.x.x.x
Friday, 13 December 2019
private ip ranges in differnt formats
192.168.0.0 - 192.168.255.255 (65,536 IP addresses)
172.16.0.0 - 172.31.255.255 (1,048,576 IP addresses)
10.0.0.0 - 10.255.255.255 (16,777,216 IP addresses)
CIDR
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
Netmask
10.0.0.0 255.0.0.0
172.16.0.0 255.240.0.0
192.168.0.0 255.255.0.0
Wildcard
10.0.0.0 0.0.0.255
172.16.0.0 0.0.240.255
192.168.0.0 0.0.255.255
Tuesday, 10 December 2019
wildcard cert on firepower FTD
In this case the wildcard was installed on a windows server (exchange)
I opened mmc
added the certs snap in
Found the wildcard cert
Exported it with the private key (set a password)
Exported PFX
In firepower went to objects -> PKI -> cert enroll
Selected import from PCKS12 files
Now go to devices certficates -> add
Now go to devices -> VPN -> Remote access
Edit the anyconnect profile
Access interfaces tab
Change the two entries SSL and IKEv2 and select the new cert
Save + Deploy
Wednesday, 4 December 2019
setup netflow on cisco 9300 stack
x.x.x.x = your netflow collector eg solarwinds etc.
flow exporter NETFLOW-EXP-TO-ORION
destination x.x.x.x
source vlan1
transport udp 2055
Setup what you want to record
flow record NETFLOW-RECORD-IN
match ipv4 tos
match ipv4 protocol
match ipv4 source address
match ipv4 destination address
match transport source-port
match transport destination-port
match interface input
match flow direction
collect interface output
collect counter bytes long
collect counter packets long
flow record NETFLOW-RECORD-OUT
match ipv4 tos
match ipv4 protocol
match ipv4 source address
match ipv4 destination address
match transport source-port
match transport destination-port
match interface output
match flow direction
collect interface input
collect counter bytes long
collect counter packets long
Setup the monitors
flow monitor NETFLOW-MON-OUT
exporter NETFLOW-EXP-TO-ORION
cache timeout inactive 10
cache timeout active 60
record NETFLOW-RECORD-OUT
flow monitor NETFLOW-MON-IN
exporter NETFLOW-EXP-TO-ORION
cache timeout inactive 10
cache timeout active 60
record NETFLOW-RECORD-IN
Enable the monitors on the interfaces
Enable under the interfaces you want to collect netflow data from usually these will be uplinks, links to other sites etc
interface GigabitEthernet2/0/36
ip flow monitor NETFLOW-MON-IN input
ip flow monitor NETFLOW-MON-OUT output
Don't forget to write your config.
You might need to check firewall rules between the two hosts.
Allow a few minutes for the data to populate in the collector.
Wednesday, 27 November 2019
creating a script to import multiple IP's into palo alto firewall
You can use excel to generate the objectname[x]
Create the address objects
set address [address-name] ip-netmask [ip-address]
eg
set address malware-ip1 ip-netmask x.x.x.x
set address malware-ip2 ip-netmask y.y.y.y
Assign the objects to a group
set address-group [address-group-name] static [address-name]
eg
set address-group malware-ips static malware-ip1
set address-group malware-ips static malware-ip2
Once I have my script
Connect to the CLI of the palo and paste it in
I have found it only allows you to paste 80 lines or so
Sometimes I need to split up my pastes but it works for me haven't had time to look into it
Once you've got it all in there don't for get to commit
Now you can go back to the web interface / GUI and create a rule with the new address group which should contain all your IP's
Tuesday, 29 October 2019
create sub ordinate CA in firepower
The Firepower SSL Decryption feature allows you to block encrypted traffic without inspection or inspect encrypted that would otherwise be unable to be inspected. In order for the FTD to decrypt the traffic the FTD must resign all certificates of websites, this is achieved by a Man in the Middle (MITM) attack. An internal CA must be used to issue a certificate using the Subordinate Certificate Authority template; Firepower will then dynamically create a certificate on the fly (spoofing the real certificate) thus allowing for decryption and inspection of the website. The client computer must trust the Internal CA so as not to receive any certificate errors.
In this scenario an FTD v6.2.2 is acting as the gateway that will decrypt the traffic, all configuration will be made on the FMC v6.2.2.
Firepower Certificate
- On the FMC navigate to Objects > Objects Management > PKI > Internal CAs
- Click Generate CA
- Fill out the information
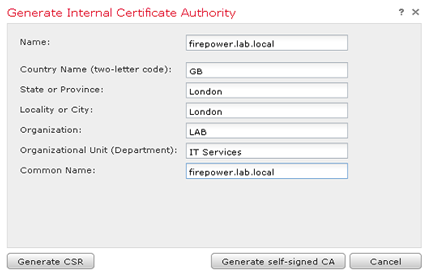
- Click Generate CSR
- Copy the CSR request content

- Navigate to the Certificate Authority (in this instance we are using Microsoft CA)
- Click Request a certificate

- Click advanced certificate request

- Paste the CSR into the Saved Request box
- From the Certificate Template drop-down box select Subordinate Certification Authority

- Click Submit
- Select Base 64 encoded and download the signed certificate (save somewhere to import later)

- Return to the FMC GUI and navigate to Objects > Objects Management > PKI > Internal CAs
- Edit the CA object previously created

- Click Install Certificate

- Click Browse and select the downloaded signed certificate
- Click Save
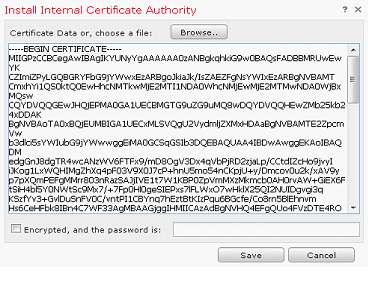
- If imported correctly the output will confirm

SSL Policy
For demonstration purposes in this example SSL Policy we will create 3 SSL rules: – Block insecure certificates (self signed, revoked and expired), Decrypt using DN and Decrypt using Application
- On the FMC navigate to Policies > Access Control > SSL
- Click Add a new policy
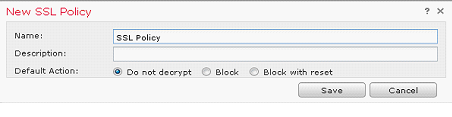
- Click Add Rule
- Enter a descriptive name e.g Insecure
- From the Action drop down list select Block with reset
- Click the Cert Status tab
- Select the certificate status to block:- revoked, self
signed and expired - Click Logging and enable Log at End of Connection
- Click Save

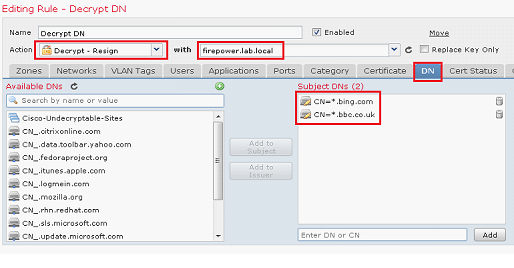
- Click Add Rule
- Enter a descriptive name
- From the Action drop down list select Decrypt – Resign
- Select the certificate to use
- Click the DN tab
- Enter a wildcard DN for websites to decrypt
- Click Logging and enable Log at End of Connection
- Click Save
- Click Add Rule
- From the Action drop down list select Decrypt – Resign
- Select the certificate to use
- Click the Applications tab
- Select the applications – in this instance we will block Google and Yahoo! Applications
- Click Logging and enable Log at End of Connection
- Click Save

- Ensure the default action is Do not decrypt

Access Control Policy
The SSL Policy must be referenced in the Access Control Policy that is applied to the FTD.
- Navigate to Policies > Access Control > Access Control
- Select the ACP applied to the FTD
- Click the Advanced tab
- Edit the SSL Policy Settings
- From the drop-down list select the previously created SSL Policy

Once the SSL Policy has been attached to the Access Control Policy the Policy can be deployed to the FTD.
Thursday, 24 October 2019
error message about silo drain on FTD
And look the option for "connection events"
Then run the following commands as root (expert sudo su):
#pmtool RestartById SFDataCorrelator
#pmtool RestartById diskmanager
Friday, 11 October 2019
troubleshoot cisco anyconnect
Wednesday, 9 October 2019
anyconnect syslog ids for logon logoff
Wednesday, 14 August 2019
Thursday, 11 July 2019
web pages are slow to load
Couldn't see any issues on the network.
Had to look on the client to see the issue present itself.
We could see source and destination server were communicating in good time but the web page was taking a long time to display.
I compared our site load time with https://tools.pingdom.com/ (or any external connection)
In chrome go into developer tools and look on the network tab for the load time
I found the site was trying to load google analytics waiting 20 seconds sometimes.
I needed to allow the following URLs on port 443 to fix the issue
ssl.google-analytics.com
www.google.com
www.google-analytics.com
Thursday, 4 July 2019
ping response meanings from cisco devices
| ! | Each exclamation point indicates receipt of a reply. |
| . | Each period indicates the network server timed out while waiting for a reply. |
| U | A destination unreachable error PDU was received. |
| Q | Source quench (destination too busy). |
| M | Could not fragment. |
| ? | Unknown packet type. |
| & | Packet lifetime exceeded. |
Tuesday, 18 June 2019
copy file to switch with xmodem
power it back on
hold the mode button in when you see xmodem is "available"
hold for about 3 seconds, and release, boot process should be interrupted. Its a bit different for each switch so google the model.
connect the console with minicom
set BAUD 115200
screen will freeze, close minicom
connect back like so
screen /dev/ttyUSB0 115200
copy xmodem: flash:/filename.bin
now press ctrl +a and then :
exec !! sx filename.bin
my file was located in /home/myuser
Some rommons can use TFTP which would be faster, you plug your
laptop lan -> mgmt port on sw set static IP on laptop (10.10.10.1) run tftpd server and drop ios in there set IP_ADDR 10.10.10.2/255.255.255.0 ping to verify emergency-install tftp://10.10.10.1/filename.bin
or
copy tftp:/filename.bin flash:
Thursday, 30 May 2019
PM-4-ERR_DISABLE link flap error detected when plugging in fibre on cisco switch
lvl1 sw -> lvl2 sw
When I plugged in the fibre I could see the light was making it to the upstairs but when plugging the fibre cable into the switch on lvl2 the port was going into err-disable with the reason as link flap.
The cause of the issue was the wrong type of fibre cable was used in the fibre patch. Single mode cable was used. When my switch transceiver (10Gig-SR multimode) and fibre patches leads were OM3 multimode.
The core of single mode fibre is much narrower than multimode so they can't work together too much light (signal) is lost.
There are two fixes and both will probably cost you:
1 - re-run the fibre patch cables with multimode cable (OM3 or higher). Range is 300m so this is what is used inside most buildings. If you need a cable run longer then you have to use single mode.
2 - Buy single mode transceivers LRM and single mode patch cables. The single mode transceivers and cables are more expensive.
https://en.wikipedia.org/wiki/Single-mode_optical_fiber
Tuesday, 30 April 2019
You see First TCP packet not SYN (tcp-not-syn) in asp drop table capture
All VPN's were up and ACL rules looked good.
We took some captures saw the traffic going out and back but not arrvinng on the branch firewall. Looking at the asp drop table we saw tcp-not-syn. It was like the branch office could not see the return traffic was part of an existing TCP connection.
We telnet'd to the web site on 443 but using the web browser didn't work. The issue in the end was MTU.
The MTU on the branch site was set quite low 1340.
Thursday, 25 April 2019
download pcap file that was created in the FTD CLI
system support diagnostic-cli
copy /pcap capture:cap-name
now go into normal FTD cli
expert mode
cd /ngfw/mnt/disk0/
cp cap-name.pcap /ngfw/var/common/
Now you can download inside.pcap from the web gui
Devices -> Device MGMT -> Troubleshoot icon on FTD -> Advanced Troubleshooting
Its also possible to copy off with the copy command to scp/tftp
Wednesday, 24 April 2019
how to reset Philips hue bulb when using with amazon echo plus / alexa
The echo plus has a built in bridge so I don't want to buy the Philips bridge.
Afterwards I couldn't add my Philips hue bulbs back, very annoying.
You need to reset the bulbs first.
1 Get the serial from the bulb.
2 Make sure its on, only reset one bulb at a time.
3 With the amazon alexa app on the phone, there is one master user. This is usually the phone/account that originally setup the echo. You need to use that smart phone.
4 Reset the bulb in the app
Start the alexa app on the smartphone
Go to devices in the bottom right
Tap the "plus" symbol in the top right
Add device
Tab "Light"
Scroll down to "Other"
Make sure the light is on
Tab "Discover devices"
This will fail, just wait for it
Now tap "Get help connecting"
Scroll down and tab "RESET PHILIPS HUE LIGHT"
Enter the serial number we took off the bulb earlier
Tap "Continue"
The echo should reset the bulb it should flash. Alexa should automatically discover it afterwards but if it doesn't try ask alexa to "discover my devices" again
Hope that helps.
Tuesday, 9 April 2019
packet capture on F5
tcpdump -i eth0 -s0 host 192.168.1.50 and host 192.168.1.100 -w /var/tmp/packet-capture.pcap
tcpdump -s0 -nni 0.0:nnnp -w /var/tmp/MYCAP.pcap host 192.168.10.100 and 192.168.20.200 -v
Copy your .pcap file off with win scp and open in wireshark
or read on CLI (on F5 is seems to take a long time to load the cap)
tcpdump -r /var/tmp/packet-capture.pcap
Monday, 1 April 2019
enable auditing/logging on NPS/radius server
Event viewer -> Custom Views\Server Roles\Network Policy and Access Services
Run CMD as administrator
Check if its on
auditpol /get /subcategory:"Network Policy Server"
If it shows "no auditing" its off
Switch it on (run CMD as admin)
auditpol /set /subcategory:"Network Policy Server" /success:enable /failure:enable
netsh trace tool on windows
Re-produce the issue
To stop the trace :
Netsh trace stop
Friday, 15 March 2019
use regular expressions to find IP addresses
https://regexr.com/
How to find IP the quick way and the exact way
https://www.regular-expressions.info/ip.html
Find IP (this will find 999.999.999.999 but you might not care
\b\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}\b
Below I was looking for 192.168.x.x
(192.168.)\d{1,3}\.\d{1,3}
Notes:
\b allows you to perform a "whole words only" search using a regular expression in the form of \bword\b. A "word character" is a character that can be used to form words. All characters that are not "word characters" are "non-word characters".
\d look for a digit
\d{1,3} look for between 1 to 3 digits
(192.168.) look for a group "192.168."
Wednesday, 13 March 2019
configure firepower FTD in CLI
Give the management interface an IP address followed by the subnet mask and the gateway
configure network ipv4 manual 192.168.100.200 255.255.255.0 192.168.100.254
Add the manager (FMC)
configure manager add 192.168.100.253 123456
Now go to FMC and add the sensor (192.168.100.200)
You might need to add a route for the network on the FMC under System -> configuration -> Management interfaces
disable http2 on cisco firepower FTD/FMC for ssl decryption
I was getting an error in the browser ERR_SSL_VERSION_INTERFERENCE
This is because the FTD tells the web server that it supports http2 which it actually doesn't so you have to disable that and use http1.1
From Cisco TAC:
Here is the command regarding disabling HTTPv2.0 on firepower:
> system support ssl-client-hello-tuning extensions_remove 16,13172
Then you need to restart snort using following command on expert mode, this will cause network outage for a few seconds
>expert
# sudo pmtool restartbytype snort
Thursday, 7 February 2019
move from type 5 or 7 passwords to type 9 on cisco router
username admin algorithm-type scrypt secret cisco(this is type 9 and best at time of writing) Wednesday, 6 February 2019
Wednesday, 16 January 2019
dealing with rouge dhcp server / arp poisining
Windows script
https://gallery.technet.microsoft.com/Check-for-Rogue-DHCP-Server-35e8c73d
linux
https://superuser.com/questions/750359/check-if-a-dhcp-server-existing-in-my-network-using-bash
arpwatch
https://www.cyberciti.biz/faq/how-to-detect-arp-spoofing-under-unix-or-linux/
sharp
http://seclist.us/sharp-a-tool-to-detect-any-arp-spoofingmitm-incident.html